Click each project title to expand the project details.
CODEBREAKERS: CULTIVATING ELEMENTARY STUDENTS’ INTEREST IN CRYPTOGRAPHY AND CYBERSECURITY EDUCATION AND CAREERS
Nelms Institute Contact: Pavlo “Pasha” Antonenko
This project introduces a new technology-enhanced STEM education model for engaging upper elementary students in cybersecurity and morphological awareness experiences, and STEM identity development in the new and exciting context of making and breaking secret codes. This project focuses on designing a cryptography-focused curriculum and mobile games for after school programs that work with elementary students. Introduction to IoT security for kids is an important module in this curriculum.
HARDWARE IP PROTECTION THROUGH PROVABLY SECURE STATE-SPACE OBFUSCATION
Nelms Institute Contact: Swarup Bhunia
Hardware intellectual property (IP) cores are the most essential part of the system-on-chip (SoC) design flow. IPs are vulnerable to a numerous threat e.g., piracy, cloning, counterfeiting, reverse engineering, Trojan insertion, etc. which makes it difficult for the IP vendors to protect their IPs from unauthorized or malicious usage. We propose a novel, scalable, and considerable overhead methodology to provide effective prevention against IP piracy and reverse engineering by netlist level obfuscation. We transform the underlying finite state machine of the design to insert authentication mechanism and expand the state space, which in general is small and prune to state traversal. Due to the expansion of the state space and insertion of authentication mechanism, it becomes difficult for an attacker to re-use or clone the IP for unauthorized use. Additionally, expanded state space hinders reverse engineering of the IP which essentially makes the design resilient to piracy.
MATERIAL BIOMETRICS: NQR SENSITIVE EMBEDDED SIGNATURES FOR AUTHENTICATING ADDITIVELY MANUFACTURED OBJECTS
Nelms Institute Contact: Swarup Bhunia
Automatic recognition of unique characteristics of an object can provide a powerful solution to verify its authenticity and safety. It can mitigate the growth of one of the largest underground industries – that of counterfeit goods – flowing through the global supply chain. In this article, we propose the novel concept of material biometrics, in which the intrinsic chemical properties of structural materials are used to generate unique identifiers for authenticating individual products. For this purpose, the objects to be protected are modified via programmable additive manufacturing of built-in chemical “tags” that generate signatures depending on their chemical composition, quantity, and location. We report a material biometrics-enabled manufacturing flow in which plastic objects are protected using spatially-distributed tags that are optically invisible and difficult to clone. The resulting multi-bit signatures have high entropy and can be non-invasively detected for product authentication using 35Cl nuclear quadrupole resonance (NQR) spectroscopy.
SURF: JOINT STRUCTURAL FUNCTIONAL ATTACK ON LOGIC LOCKING
Nelms Institute Contact: Swarup Bhunia
To help protect hardware Intellectual Property (IP) blocks against piracy and reverse engineering, researchers have proposed various obfuscation techniques that aim at hiding design intent and making black-box usage difficult. A dominant form of obfuscation, referred to as logic locking, relies on the insertion of key gates (e.g., XOR/XNOR) at strategic locations in a design followed by logic synthesis. Recently, it has been shown that such an approach leaves predictable structural signatures, which make them susceptible to machine learning (ML) based structural attacks. These attacks are shown to deobfuscate a design by learning the deterministic nature of transformations incorporated by commercial synthesis tools. They are attractive for unraveling the design intent. However, they may not be able to provide a working design. In this paper, we introduce a novel attack on obfuscation techniques, called Structural Functional (SURF) attack, which, for the first time to our knowledge, accomplishes key extraction through scalable functional analysis while leveraging the output of structural attacks. We have developed complete flow and an automatic tool for the attack, which shows promising results. We are able to retrieve, on average, ~90% keybits for obfuscated ISCAS-85 benchmarks (100% in several cases) with > 98% output accuracy. We observe that SURF attack, unlike any known attack, can enable both discovering design intent as well as black-box usage. It is effective for all major variants of logic locking; scalable to large designs; and unlike SAT based attacks, is effective for all design types (e.g., multipliers, where SAT based attacks typically fail).
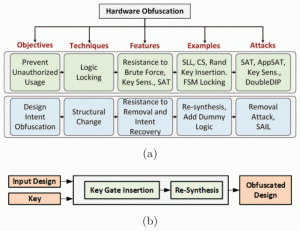
TRUSTED AND ASSURED HARDWARE FOR IOT
Nelms Institute Contact: Swarup Bhunia
Dr. Swarup Bhunia and his team are developing standalone Computer-Aided Design (CAD) tools for evaluating trust and assurance for Internet-of-Things (IoT) hardware at all levels. These tools include custom data-structures and algorithms for scalable and efficient processing of large designs at different levels of abstraction, metrics for informative and comprehensive understand- ing of hardware trust and assurance as well as vulnerabilities, and red and blue dynamic bench- marking for robust data analytics and evaluation on several state-of-the-art attacks and defenses.
PCB-LEVEL TROJAN INSERTION SYSTEM
Nelms Institute Contact: Swarup Bhunia
In this project, Dr. Swarup Bhunia and his team are developing a comprehensive platform encompassing both software and hardware regime for PCB Trojan benchmarking to effectively evaluate emerging solutions for PCB assurance in an untrusted supply chain. The CAD tool uses Trojan templates to automatically find suitable locations within any input PCB design through functional/ structural analysis for Trojan insertion. This software suite is expected to include a large representative dataset on the possible attack space of synthetic PCB Trojan benchmarks for commercial PCB designs. Such a framework enables an unbiased and comparable evaluation of various countermeasures. Additionally, Dr. Bhunia’s team is developing a flexible and scalable PCB-level emulation system to insert and activate hardware Trojans in modern intricate computing devices.
MEMORY IN LOGIC PUF
Nelms Institute Contact: Swarup Bhunia
Physical Unclonable Functions (PUFs) are a security primitive used for securing, identifying, and authenticating a device. However, current PUF designs on FPGAs can be challenging to implement or incur significant overhead. This often limits their implementation into System on Chip (SoC) designs or other FPGA applications. As such, we propose the Memory in Logic PUF (MeLPUF) a low overhead, distributable PUF which that leverages the existing logic gates which make up the reconfigurable architecture in an FPGA. These on-demand memory cells can be dispersed across the combinational logics of various intellectual property (IP) blocks in an SoC design to achieve distributed authentication. They can also be synthesized with a logic synthesis tool to incorporate and meet the power and area restrictions of a design.
HARDWARE AWARE SOFTWARE TIMING ATTACK EVALUATION (HASTE)
Nelms Institute Contact: Swarup Bhunia
Dr. Swarup Bhunia and his team are developing an automated framework for the assessment of timing side-channel leakage for a given software running on a given microarchitecture. This work aims to leverage knowledge of the underlying hardware microarchitecture along with software analysis to identify regions of code that are vulnerable to timing side channels.
DECENTRALIZED DETECTION OF CYBER ATTACKS AGAINST MICROGRID ENERGY
Nelms Institute Contact: Zoleikha Biron
This project aims at developing the scientific foundations and the design methodologies for autonomous detection of cyber-attacks against energy management systems in microgrids. The objectives of this project include: (i) developing a comprehensive study on the security of micro- grids; (ii) designing a cooperative and distributed methodology to detect cyber-attacks against different units of the microgrid; and (iii) reducing the number of misdetections due to the inevitable uncertainties in system parameters, volatile renewable generation and customer demand profiles. Microgrids are uniquely different from bulk power systems, structurally and operationally. The uniqueness of microgrids makes it significantly more challenging to detect anomalies under cyber-attacks, using the conventional large-scale power system techniques. In this regard, we introduce a distributed framework to enable autonomous detection of cyber-attacks at the unit level using each unit previous observed knowledge of the surrounding microgrid environment. The autonomous unit detection scheme is enforced with the adaptive threshold algorithm to avoid midsection and reduce false-positive alarms.
CNS CORE: SMALL: A HARDWARE/SOFTWARE INFRASTRUCTURE FOR SECURED MULTI-TENANCY IN FPGA-ACCELERATED CLOUD AND DATACENTERS
Nelms Institute Contact: Christophe Bobda
The goal of this project is the secure sharing of FPGA resources in multi-tenancy cloud that incorporate FPGAs for hardware acceleration. The research focuses on three subproblems to enable a transparent utilization by cloud tenants: virtualization, FPGA resource management and domain separation. Virtualization is addressed through a combination of paravirtualization, hardware acceleration and dynamic network on chip infrastructure on the FPGA for unrestricted placement of IP tasks at run-time. FPGA resource management is tackled by integrating the spatial and temporal placement paradigm in the cloud management framework. Effort is placed on the design of temporal placement strategies to better allocate accelerators on one or multiple FPGAs at run-time. Isolation is achieved using the FLASK architecture and ensuring that IP inherits security domain policies of the VMs to which they belong. Project result will be validated using a 20-nodes FPGA-accelerated cloud designed and deployed at the University of Florida.
SCH: INT: COLLABORATIVE RESEARCH: CROWD IN ACTION: HUMAN-CENTRIC PRIVACY-PRESERVING DATA ANALYTICS FOR ENVIRONMENTAL PUBLIC HEALTH (NSF)
Nelms Institute Contact: Yuguang “Michael” Fang
This project serves as a training ground for educating future decision-makers and workforce on privacy-preserving healthcare technologies. This multidisciplinary research advances the state-of-the-art public health by combining multi-scale data collection and analysis. Specifically, the project redesigns current healthcare monitoring systems for both severe infectious diseases and long-term environment-related diseases and their exacerbation (e.g., air pollutant-induced pulmonary diseases, such as chronic obstructive pulmonary disease and lung cancer). By considering the high sensitivity and distributed manner of the data from patients and users, this project addresses the privacy preservation in two-fold: 1) completely redesign efficient collaborative classification schemes by applying novel metrics without leaking individual’s privacy; and 2) introduce new architectures to perform crowdsourcing data analysis by using light-weighted and verifiable encryption schemes. This project also grounds the theoretical outcomes to actual crowdsensing systems and social networks for validation. Finally, a new methodology on public health prediction model is developed with practical systematic implementation in healthcare systems.
CAREER: A UNIFIED THEORY OF PRIVATE CONTROL SYSTEMS
Nelms Institute Contact: Matthew Hale
This project will develop new differential privacy mechanisms and novel privacy/performance tradeoffs for several classes of control systems, and it will deploy all of these theoretical developments to sensory data gathered at the UF Innovation Hub, which is a smart building on campus.
RESILIENT SYSTEM-ON-CHIP ARCHITECTURE
Nelms Institute Contact: Sandip Ray
System-on-Chip (SoC) design involves composition of pre-designed hardware blocks into a single integrated circuit. SoCs are readily being applied in various domains like healthcare, cyber-physical systems, automotive, etc. A modern SoC design includes a variety of processor cores, memory systems, cryptographic blocks, communication modules (e.g., wireless and LTE modules), debug and peripheral driving interfaces (e.g., JTAG, HDMI, etc.), power management units, and many others. The individual hardware blocks, referred to as intellectual properties (“IP” for short) are procured through a global supply chain of IP vendors. System functionality is implemented through communication of IPs through a variety of system interconnects. SoC designs promise much faster design time, robustness, and configurability than custom hardware. Unsurprisingly, SoC designs have seen explosive proliferation in electronic computing system architectures, particularly as we move into the era of hundreds of billions of devices. A key concern with the proliferation of SoC designs is security. As we move towards Internet-of- Things, these systems are continually tracking, analyzing, and communicating some of our most intimate personal information, including sleep patterns, health, location, etc. In addition to private end-user information, they also sensitive information in modern SoC designs include security-critical parameters introduced during the system design, e.g., fuses, cryptographic and Digital Rights Management (DRM) keys, firmware execution flows, on-chip debug modes, etc. Sensitive information or data in a modern computing system will be collectively referred to as “assets”. Unauthorized or malicious access to these assets can result in leakage of company trade secrets for device manufacturers or content providers, identity theft for end users, subversion of national security, and destruction of human life. It is vital to our well-being to ensure that these assets in computing devices are protected from unauthorized, malicious access. The goal of this project is to enable a streamlined, disciplined approach for implementing and validating diverse security requirements in modern SoC designs. A key contribution of the project has been the establishment of an architectural framework for implementing a spectrum of security policies, including access control, information flow, time-of-check vs. time-of-use, etc. The framework introduces a centralized policy implementation IP that communicates with the various hardware modules in the SoC design to implement target policies. We demonstrated how the architecture can facilitate implementation of diverse security requirements (even in the presence of untrusted IPs) and streamline their validation. The approach holds the promise to usher in a new “patchable” SoC architecture, i.e., systems developed with hardware that can be reconfigured and updated in field just like we can update software or firmware components.
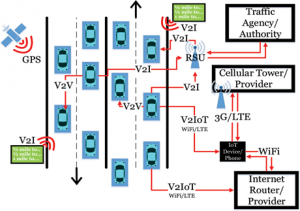
SECURITY ASSURANCE FOR AUTONOMOUS VEHICULAR COMMUNICATIONS
Nelms Institute Contact: Sandip Ray
How would you feel if a hacker could remotely push a button that would cause your vehicle to veer off the highway into a ditch? Research over the last decade has shown that not only is this possible but it is actually depressingly easy for a trained hacker to do so. The reason is that as vehicles get infused with electronics and software to support and create various autonomous features, they are starting to look more like computers than as traditional cars. That also means that they are inheriting the problems that have plagued computers for decades – cyber-security. The only difference in this case is that vehicles are more like computers driving at 70 miles/hour and with people inside. Cyber-attacks on these systems can cause catastrophic accidents, cost human life, and bring down transportation infrastructure. As we increase autonomous features of vehicles and move toward self-driving cars, we are sorely in need for a robust vehicular design that is resilient to cyber-attacks.
A key feature of emergent vehicles is connectivity. Vehicles can “talk” to other vehicles as well as with the transportation infrastructure through sensors and inter-vehicular communications (called V2X) to enable smooth and efficient traffic flow and infrastructure utilization. Connected autonomous vehicle (CAV) applications are designed today include platooning, cooperative collision detection, cooperative on-ramp merging, etc. Connectivity, however, is also one of the most vulnerable components of autonomous vehicles and one of the crucial entry points for cyber-attacks. A key feature of such attacks is that they can be conducted without requiring an adversary to actually hack into the hardware/software or physical components of the target vehicle. They can simply send misleading or even malformed communications to “confuse” the communication or sensor systems.
The goal of this project is o address this crucial problem of cyber-resiliency of CAV applications. A key result from the team is a unique AI-based resiliency architecture against arbitrary cyber-attacks on perception channels (e.g., communication and sensor channels). To our knowledge this is the first (and so far, the only) comprehensive resiliency framework for connected vehicle applications against arbitrary cyber-attacks. The architecture exploits recent advances in AI and machine learning to create a unique, on-board predictor to detect, identify, and respond to malicious communications and sensory subversions. A unique feature of the approach is that it can provide assured resiliency against a large class of adversaries, including unknown attacks. We have instantiated the approach on several CAV applications and developed an extensive experimental evaluation methodology for demonstrating such resiliency.
POST-SILICON VALIDATION
Nelms Institute Contact: Sandip Ray
The size and complexity of a modern electronic computing systems precludes catching all design errors by functional verification (formal or otherwise) only on pre-silicon models. Indeed, an estimated 50% of modern SoC designs contain functional errors in the first fabricated silicon. Consequently, post-silicon verification has become a critical component of the overall verification flow. Post-silicon verification entails running simulation on first-pass fabricated silicon to detect functional bugs which are missed during pre-silicon validation. Since post-silicon execution proceeds at target clock speeds, it permits a much deeper exploration of the design space than afforded by pre-silicon. However, a key challenge in post-silicon verification is limited observability: only a few of the thousands of important internal signals are observable during normal chip operation. Observability is constrained by the number of pins and size of available internal buffers in the design. The situation is exacerbated by the current architectural trend away from a conglomeration of individual chips aggregated within a motherboard towards System-on-Chip (SoC) designs with system functionality within a single silicon substrate: with high integration afforded by the SoC architecture, the number of pins and correspondingly external observability, is getting increasingly diminished.
The goal of this project is to streamline and systematize post-silicon validation of hardware systems targeted towards current and emergent applications. We aim to develop a comprehensive TFM (tool, flow, methodology) with (1) effective and scalable algorithms for selection and qualification of post-silicon observability that affords amelioration of the limited observability problem without reduction in validation quality, (2) automation in post-silicon triage and diagnosis, and (3) a formally guaranteed post-silicon coverage. Finally, we are investigating clear and tight connection between pre-silicon and post-silicon validation to facilitate comprehensive assurance of system functionality and performance.
AUTOMATICALLY VALIDATING SOC FIRMWARE THROUGH MACHINE LEARNING AND CONCOLIC TESTING
Nelms Institute Contact: Sandip Ray
Recent years have seen a dramatic increase in the size and complexity of firmware in both custom and SoC designs. Unlike custom hardware, a system functionality implemented through firmware can be updated after deployment in response to bugs, performance limitations, or security vulnerabilities discovered in-field, or for the purpose of adapting to changing requirements. Today, it is common to find more than a dozen hardware blocks (also referred to as “intellectual properties” or “IPs”) in a commercial SoC design implementing significant functionality through firmware that execute on diverse microcontrollers with different instruction set architectures, e.g., IA32, ARMTM, 8051, etc., as well as proprietary custom instruction set. Firmware implementations are particularly common for many core algorithms in machine learning systems, since these algorithms typically need to be adapted and updated in-field in response to evolving data patterns, workloads, and use cases throughout the lifetime of the system. Given this extensive use, it is getting increasingly crucial to ensure that the firmware implementations are functionally correct, robust against various microarchitectural side channels, and protected against malicious security exploitation.
The goal of this project is to develop an automated framework for dynamic firmware validation that enables exploration of subtle hardware/firmware interactions while maintaining the scalability and performance. Our approach exploits some key insights from formal techniques to achieve scalability in test generation. It involves innovative coordination of two components: (1) a configurable, plug-and-play Virtual Platform (VP) architecture that enables disciplined, on-the- fly selective refinement of hardware modules from VP to RTL; and (2) a concolic test generation framework that combines symbolic analysis with machine learning for targeted exploration of firmware paths that have a high probability of exhibiting errors and vulnerabilities (if they exist). The outcome is a comprehensive, automated methodology for firmware analysis that (1) can be employed early in the system exploration life-cycle, (2) accounts for the interaction of the firmware with the underlying hardware and other IPs, and (3) enables focused, targeted exploration of firmware code to identify functional error conditions and security vulnerabilities.
MULTI-LAYER AND SYSTEMATIC ANALYTICS FOR SECURING THE INTERNET-OF-THINGS
Nelms Institute Contact: My T. Thai
By breaking a typical IoT system into application and Internet layers, we aim to build a set of monitoring, analysis, and defense capabilities that run in parallel to the IoT applications to a) perform various security analyses within a given system layer, b) use cross-layer artifacts towards detecting high-level security events. The transformative aspect of our work is the investigation of residual application- and network-layer artifacts written in applications to characterize in-depth application- and network level behaviors. Not only this will lead to amplified performance efficiencies, but also address unique and intrinsic features of IoT software that will most likely withstand software evolution.
DEEPTRUST: BUILDING COMPETENCY-AWARE AI SYSTEMS WITH HUMAN CENTRIC COMMUNICATION
Nelms Institute Contact: My T. Thai
This project aims to develop a machine learning (ML) system that combats visual misinformation such as fake/altered photos in a news context through trust-building machine-human interactions. Specifically, the project will focus on building human trust of the news diagnostics from the machine learning system through reported competency-based self-assessment and human centric explanations of the visual diagnostics. The research methods will entail: 1) an adaptive ML system that can self-assess the performance level of any classifier, with a provable guarantee, 2) an explainer that is robust to adversarial attacks and in a human-understandable, trusted form, and 3) method to assess best human-machine communication approaches in news consumption and the communication preferences of news consumers for such explainers.
EM RADIATION SUPPRESSION AND ATTACKING MITIGATION WITH OPTIMAL LAYOUT AND SHIELDING TECHNIQUES
Nelms Institute Contact: Shuo Wang
Modern high-speed variable motor drive systems are widely used in the electrification of transportation systems. These systems include both small-signal and high power systems. The high power system generates EM radiation which can induce unwanted noise in the small-signal systems. The noise can lead to system malfunction causing safety and reliability issues. Identifying the EMI radiation sources, understanding the radiation mechanism, and developing suppression techniques are extremely important in the applications of electrification of transportation.
INVESTIGATION OF EM ATTACK AND PREVENTION FOR TOUCHSCREEN ENABLED ELECTRONICS
Nelms Institute Contact: Shuo Wang
Touchscreens have been very popular in both consumer and commercial electronics since the last decade. The operation of the touchscreen is based on the sensed electric charge change. Hackers can attack the touch screen and control the Apps by performing EM attacks wirelessly. By exploring the operation of touchscreen, developing EM attack theory, and quantifying the attacking electric field strength, a touchscreen EM attack technique is discovered, demonstrated, and quantified. Corresponding prevention techniques are also proposed.
A RISK-AWARE DER MANAGEMENT FRAMEWORK WITH REAL-TIME DER TRUSTWORTHINESS EVALUATION
Nelms Institute Contact: Shuo Wang
The increasing penetration level of distributed energy resources (DERs) substantially expands the attack surface of the modern power grid. By compromising DERs, adversaries can destabilize the grid and potentially causing large-area blackouts. Due to the limited administrative control over DERs, constrained computational capabilities, and possible physical accesses to DERs, current device level defenses are insufficient to defend against malicious attacks on DERs. To compensate the shortcomings of device level defenses, in this paper, we develop a system-level risk-aware DER management framework (RADM) to mitigate the attack impacts. We propose a metric, trust score, to dynamically evaluate the trustworthiness of DERs. The trust scores are initialized with offline trust scores derived from static information and then regularly updated with online trust scores derived from a physics-guided Gaussian Process Regressor using real-time data. The trust scores are integrated into the grid control decision making process by balancing the grid performance and the security risks.
COLLABORATIVE RESEARCH: SHF: SMALL: DECENTRALIZED EDGE COMPUTING PLATFORM FOR PRIVACY-PRESERVING MOBILE CROWDSENSING (NSF)
Nelms Institute Contact: Dapeng Oliver Wu
Mobile Crowdsensing (MCS) is an important data collection paradigm that leverages natural human mobility and sensing capabilities of smartphones to achieve large spatial-temporal coverage and avoid the cost of deploying fixed sensing infrastructure. Existing works on MCS assume cloud-centric architecture that has three limitations: 1) it aggregates sensor data from all users to a centralized cloud server through a long path in the back-haul Internet network, which raises high data security concerns; 2) it localizes the collected sensor data by tracking the real-time location of each participant, which raises serious location privacy concerns; and 3) its response delay from multi-hop-away cloud may be unacceptable to some applications that require fast response of a service request. This project addresses these challenges with a new decentralized design of MCS system with novel message-passing based spatial-temporal sensor data recovery algorithms to make the MCS more secure and responsive.
SATC: CORE: SMALL: FIRMA: PERSONALIZED CROSS- LAYER CONTINUOUS AUTHENTICATION (NSF)
Nelms Institute Contact: Dapeng Oliver Wu
The goal of this project is to build and evaluate FIRMA, a personalized, user-transparent, continuous authentication framework for the Windows OS based on deep learning and the continuous collection of data across the user, operating system, and network layers. This large, heterogeneous, high-dimensional, and temporal data will be used to create a personalized user profile and a deep learning module that will predict at runtime the confidence level of a user identity. This confidence level can be used by a system administrator to determine the level of access a user/ employee can have on system resources, and detect stealthy malware and early indications of insider attacks. FIRMA’s novel deep learning module will also be able to adapt to benign changes in the user’s profile. This project will generate the following outcomes: (i) FIRMA, a personalized, user transparent, continuous authentication framework that can help organizations in identifying employees’ identity level, and detecting sophisticated malware and early indications of insider attacks, (ii) a novel deep learning classifier for detecting deviations from a user computer behavioral profile at runtime, (iii) a public, opensource cross-layer computer behavioral profile extractor, and (iv) analysis of real user profiles extracted in a ecologically-valid longitudinal study with 100 participants.
CAREER: TOWARDS A SECURE AND RELIABLE INTERNET OF THINGS THROUGH AUTOMATED MODEL EXTRACTION AND ANALYSIS
Nelms Institute Contact: Tuba Yavuz
The PI’s long-term career goal is to improve reliability and security of systems code through automated formal methods and software engineering. Recent advances in automated program verification and analysis provide a fertile ground for the proposed research. However, the complexity of systems code impedes high-coverage analysis that is required for formal guarantees. Model-driven approaches provide a rigorous methodology for designing provably secure and reliable models. However, due to a formal gap between the models and their implementations, proving preservation of reliability and security properties by the implementations remains to be a challenge. Recent studies on the insecurity of emerging Internet of Things (IoT) has resurfaced the critical gap between models and their actual implementations. The anticipated role of IoT in the quality of our daily lives call for effective solutions for this fundamental problem. This project aims to improve security and reliability of IoT through automated extraction of precise behavioral models of the IoT components and their interactions for effective and efficient reasoning about the functional and non-functional system-level properties as these systems evolve.
COLLABORATIVE RESEARCH: FMITF: TRACK I: PROPERTY- SPECIFIC HARDWARE-ORIENTED FORMAL VERIFICATION MODULES FOR EMBEDDED SYSTEMS
Nelms Institute Contact: Tuba Yavuz
Developing reliable and secure systems requires a deep understanding of the full software stack and the hardware architecture. Complexity of software and the hardware makes it very challenging to construct a comprehensive view of computing systems, which leads to overly optimistic assumptions about the software or the hardware. Despite recent advances in the decision procedures and the analysis techniques, hardware software co-verification is challenged by the scalability issue. Although run-time verification can be used potentially to overcome the scalability challenge, for embedded systems the success of runtime verification highly depends on the proper configuration. We propose a property-directed run-time verification approach that utilizes hardware software co-model extraction for improved bug detection capability, overhead, and precision.
PRE-SILICON ELECTROMAGNETIC SIDE CHANNEL ANALYSIS
Nelms Institute Contact: Shuo Wang
Side channel Analysis (SCA) is the process of analyzing unintentional signals caused by running operations in hardware, such as power draw and electromagnetic emanations, for information about the operations being performed. To secure designs from the threat of SCA, defenders often need to iterate through several post-silicone implementations of a design, which is expensive in terms of both time and money. It is also possible to simulate the electromagnetic (EM) behavior of a design, but this is prohibitively time consuming for all but the smallest of circuits. To address this, and better secure circuits, particularly those which will be routinely left physically accessible such as in IoT applications, we are exploring ways to predict EM leakage at the HDL and layout level.
HARDWARE ACCELERATOR SIDE CHANNEL ANALYSIS AND MITIGATION TECHNIQUES
Nelms Institute Contact: Shuo Wang
Side channel Analysis (SCA) is the process of analyzing unintentional signals caused by running operations in hardware, such as power draw and electromagnetic emanations, for information about the operations being performed. SCA can consistently recover confidential information from algorithms run on microprocessors. However, as hardware accelerated computation has become increasingly popular due to advances in reconfigurable computing, encryptions and other sensitive operations are more often being computed through these components. Evaluating the resilience of hardware implementation of common algorithms and creating new methods to protect and secure them from SCA, is therefore of utmost importance. To this end, we have created a highly adaptable framework for collecting side channel measurements from a variety of devices and designs. This framework also performs both traditional and AI-enhanced SCA to evaluate the security of an implementation. Using this information, we can guide efforts to enhance the robustness of a design.
CAREER: FAST FOVEATION: BRINGING ACTIVE VISION INTO THE CAMERA
Nelms Institute Contact: Sanjeev Koppal
Most cameras today indiscriminately photograph their entire visual field. In contrast, animal eyes, have fast mechanical movements that control how the scene is imaged in detail by the fovea, where visual acuity is highest. In computer vision, this idea of actively selecting where to look — i.e. active vision — has been mostly demonstrated with slow, power-hungry mechanical options for changing camera pose, such as pan-tilt-zoom motors or robot motion. The key challenge to conducting active vision for small mobile platforms is to provide fast, camera control of the physical properties that influence image formation, such as wavelength, resolution, polarization, viewpoint, exposure time, etc. This project focuses on active vision algorithms for fast adaptive resolution, generalizing the foveation capability found in animals. I propose new designs called *foveating cameras*, which work by capturing reflections off a tiny, fast mirror whose scan path allows for selective scene viewing. Foveating cameras will revolutionize sensing in mobile systems and robotics, since algorithms such as visual state estimation or object recognition can now use imagery with high resolution on every region of interest, even if these are at different depths and viewing directions.
SAIL: MACHINE LEARNING GUIDED STRUCTURAL ANALYSIS ATTACK ON HARDWARE OBFUSCATION
Nelms Institute Contact: Swarup Bhunia
Obfuscation is a technique for protecting hardware intellectual property (IP) blocks against reverse engineering, piracy, and malicious modifications. Current obfuscation efforts mainly focus on functional locking of a design to prevent black-box usage. They do not directly address hiding design intent through structural transformations, which is an important objective of obfuscation. We note that current obfuscation techniques incorporate only: (1) local, and (2) predictable changes in circuit topology. In this paper, we present SAIL, a structural attack on obfuscation using machine learning (ML) models that exposes a critical vulnerability of these methods. Through this attack, we demonstrate that the gate-level structure of an obfuscated design can be retrieved in most parts through a systematic set of steps. The proposed attack is applicable to all forms of logic obfuscation, and significantly more powerful than existing attacks, e.g., SAT-based attacks, since it does not require the availability of golden functional responses (e.g., an unlocked IC). Evaluation on benchmark circuits show that we can recover an average of about 84% (up to 95%) transformations introduced by obfuscation. We also show that this attack is scalable, flexible, and versatile.