Dr. Sandip Ray, endowed IoT term professor in the Department of Electrical and Computer Engineering and Nelms Institute faculty member, has been awarded a research grant by the Semiconductor Research Corporation (SRC). The three-year grant funds research on the project “Security Assurance for Multi-tenant Accelerators.”
Project Overview:
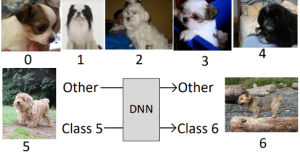
Computing has been moving into the cloud. We are no longer “owning” a computing resource like the old days. Instead we are “renting” them as a service from a cloud service provider such as AWS and Microsoft Azure. Cloud computing has several attractive features for both individuals and enterprises over upfront investment in individualized compute resources and information technology. You can have a pay-as-you-go expense model, and flexibility in upgrading and downgrading resources on a need basis. Recently, the cloud-based service models have been extended to a variety of hardware accelerators, including FPGA, GPU, and even custom ASIC, in addition to conventional CPU-based computer. However, a key issue with this new paradigm is multi-tenancy and the security issues involved. Since computing resources are rented, users of the resources now behave as tenants with the same resource shared spatially or temporally with other tenants. One must then deal with the possibility of one tenant potentially attempting to subvert other tenants.
As a simple example of security issues involved in multi-tenancy, consider one tenant hosting a Deep Learning accelerator for Computer vision in the cloud. Suppose a malicious tenant could tamper with the accelerator such that it is still functional and classifies most of the images correctly but only misclassifies one category of images into another. From an attacker perspective, the ability to do so provides endless potential to do harm, e.g., by choosing the image classes appropriately they can easily turn the Computer Vision system racist or misogynist. On the other hand, the scary fact is that tampering with the system is actually not too difficult if the adversary has the right information about the victim tenant.
“The goal of this project is to investigate security issues arising from multi-tenancy. To our knowledge it is the first comprehensive effort to systematically explore and mitigate the spectrum of security issues in cloud-based multi-tenant systems,” Ray said.
The project has three distinct goals. The first goal is to clearly understand the scope and extent of security threats posed by multi-tenancy in the first place. The second goal is to come up with new approaches to detect such threats in real time and provide mitigation. The third goal is to develop a new paradigm of multi-tenant computing where tenants can use a cloud-based shared computing infrastructure with a formal assurance that their assets and computation remains secure against other, potentially malicious, tenants using the same computing resource.
