
Underwater data centers (UDCs) hold promise as next-generation data storage due to their energy efficiency and environmental sustainability benefits. While the natural cooling properties of water save power, the isolated aquatic environment and long-range sound propagation characteristics in water create unique vulnerabilities which differ from those of on-land data centers.
In this new work called Aquasonic, a team of researchers led by Dr. Sara Rampazzi discover the unique vulnerabilities of fault-tolerant storage devices, resource allocation software, and distributed file systems to acoustic attacks. They investigate and discuss the effectiveness of standard defenses against acoustic injection attacks and propose a novel machine learning-based detection system. Aquasonic aims to help manufacturers proactively protect UDCs against acoustic attacks and ensure the security of emerging subsea computing infrastructures. The paper will appear in IEEE Security & Privacy 2024.
Read more about the research in the article below from University of Florida News.
Underwater data centers are the future. But a speaker system could cripple them.
In 2018, Microsoft plunged almost 1,000 servers more than 100 feet beneath the Scottish sea. No mere stunt, it was a test of bold plans to sustainably meet our growing appetite for cloud computing services.
By harnessing the natural cooling properties of ocean water, companies hope to dramatically cut cooling costs and emissions. But with the rise of underwater data centers comes a new threat — the potential for attacks targeting critical internet infrastructure hidden beneath the waves.
Now, new research reveals that such an attack could come from little more than a pool speaker playing a high D note.
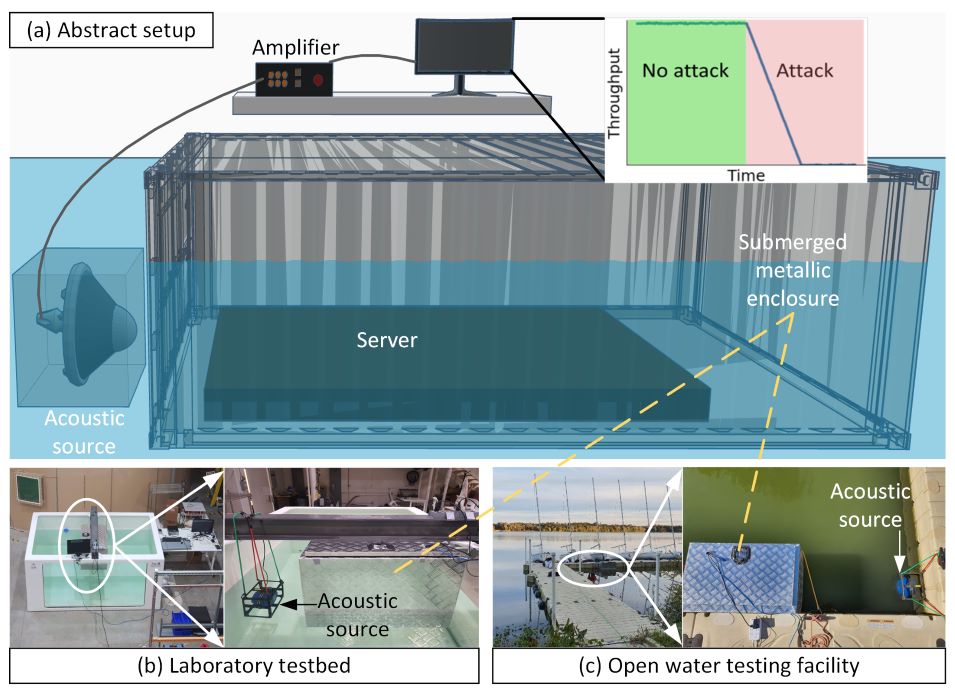
The new study from a group of cybersecurity and robotics researchers at the University of Florida and the University of Electro-Communications in Japan reveals for the first time a critical vulnerability of underwater data centers: sound. Carried by dense water, and targeting the resonant frequencies of hard drives, sound injection attacks can make servers unresponsive and crash networks. After just a few minutes, some hard drives are even permanently destroyed.
However, the scientists also developed a machine learning algorithm that can accurately identify sound attacks, allowing the system to respond before it crashes. The researchers aim to work with technology companies to improve data center security by safeguarding against attacks before they happen.
The team, led by UF Professor of Computer and Information Science and Engineering Sara Rampazzi, Ph.D., shared their findings on acoustic attacks in a paper presented May 20 at the 45th IEEE Symposium on Security and Privacy, an international cybersecurity conference.
“The main advantages of having a data center underwater are the free cooling and the isolation from variable environments on land,” said Md Jahidul Islam, Ph.D., a professor of electrical and computer engineering at UF, an expert in marine robotics, and co-author of the paper. “But these two advantages can also become liabilities, because the dense water carries acoustic signals faster than in air, and the isolated data center is difficult to monitor or to service if components break.”
In tests both in a laboratory water tank and in a lake on the UF campus, researchers showed that an off-the-shelf speaker for playing music in pools tuned to five kilohertz — a frequency designed to make hard drives vibrate uncontrollably and one octave above what can be played on a piano — could cause networks to crash by disrupting their reliability.
The attack was accomplished from 20 feet away. With some simple underwater robotics, Islam said, attackers could disrupt data centers from miles away, further concealing their efforts.
After demonstrating the power of acoustic attacks, the scientists tested different defenses. Sound-proof panels raised the servers’ temperature too much, countering the advantages of cooling with water. Active noise cancellation, the technology behind noise-canceling headphones, was too cumbersome and expensive to add to every data center.
The team, which included University of Electro-Communications professor Takeshi Sugawara, landed on a software solution. Using machine learning, they developed an algorithm that could accurately identify the pattern of disruption caused by acoustic attacks. With additional programming, this algorithm could allow networks to minimize the damage by reallocating computational resources before an attack can crash the system.
Underwater infrastructure is always at risk, and sabotage can be difficult to trace. In February, internet traffic between Europe, Africa and Asia was disrupted when underwater fiber optic cables in the Red Sea were cut, possibly by rebels. And following Russia’s invasion of Ukraine in 2022, unknown actors destroyed an underwater gas pipeline between Russia and Germany with explosives. No country or group has claimed responsibility, and the attack heightened tensions between Europe and Russia and forced changes in Europe’s energy-generation plans.
Unlike explosives, acoustic attacks on data centers could be subtle. “The difference here is an attacker can manipulate the data center in a controlled way. And it’s not easy to detect,” Rampazzi said.
Companies may even need to protect against accidental disruption.
“The ocean is awash in sound already. We’ve demonstrated that these attacks can happen inadvertently from something like a submarine sonar blast, which is extremely loud,” said co-author Kevin Butler, Ph.D., a UF professor and director of the Florida Institute for Cybersecurity Research. “So it’s that much more important that we know how to defend against these attacks. These are issues that haven’t been studied at all by the security community.”
Two years after Microsoft submerged their data center, they hauled it to the surface, the test complete. Failure rates in the controlled environment were eight times lower than on land, and the infinite supply of cold ocean water reduced cooling costs. Underwater data centers seem to be the future — so long as they are protected.
This work was supported in part by the National Science Foundation and the U.S. Air Force.
May 6, 2024
Originally published on University of Florida News.